Cybersecurity Skills Gap: Will it improve or widen further?
There is a fast approaching shortage of workers in the workforce across a multitude of industries—and while many think of the healthcare industry as being the most threatened by this shortage as there has been a recent lack of future qualified nurses, there is an alarm being sounded by the cybersecurity industry for fear of the same thing happening within it as well. As the number of cyber threats facing internet users globally increases daily, so does the demand for qualified individuals to combat these risks. While demand for cybersecurity jobs is expected to grow by 53% over the next two years, there are not enough adequately qualified people expected to be available to fill all of these positions. This is what is known as the cybersecurity skills gap.
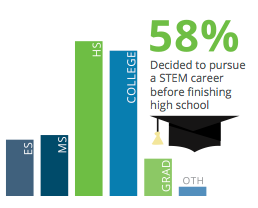
As of March of 2015, there were more than 209,000 cybersecurity jobs in the US that went unfilled and the number has grown drastically since then. Most experts believe this to be caused by a lack of interest by future workers, meaning that not only is there a lack of attention towards this industry among college-aged students who are not picking cyber-related majors such as Computer Information Systems and Computer Science, but K-12 children as well. In an attempt to increase interest, there are programs such as STEM (science, technology, engineering, and math) that are designed to peak a young tech guru’s curiosity about the possibility of pursuing a career in the IT industry. While some may be interested in a career in cybersecurity, not everyone who tries is adequately qualified for the position which they are applying; for this reason, experts in the field are divided on whether or not the cybersecurity skills gap will improve or be widened further.
Will the gap improve or widen further?
Experts are torn on their opinions as to whether or not the cybersecurity skills gap will be improved or widened in the coming years.
Those who believe that there is no hope for the industry’s workforce to improve argue that while many people may be applying for IT jobs, they are not properly qualified for these positions. Sixty-seven percent of IT professionals do not have any certification that would make them qualified for their jobs—they must simply learn while they are on the job. These naysayers also argue that most of the executives that prioritize cybersecurity are only CIOs and senior IT leaders, prioritizing the threat about 73% compared with CEOs and CTOs who reportedly only consider security approximately 55% of the time on average between the two positions. The experts on this side of the issue believe that if these high ranking executives don’t take the threats that face their companies seriously, how can the gap be improved properly?
Those who believe that the gap will be decreased have two main approaches to improving the industry’s lacking workforce. First, is a people-centric approach that focuses on training our next generation of workers in cybersecurity skills. This requires teamwork between industry professionals and higher education establishments who must not only share the responsibility, but are required to have a cohesive action plan. In May of 2016, IBM security professionals volunteered their time to teach at the University of Warwick to discuss things like security solution design processes as well as endpoint security among others. By educating those interested in a career in IT, the gap will surely be lessened over time.
The second approach that supporters of the skills gap being closed might utilize, primarily as a backup plan (for now), is the use of cybersecurity robot workers. This approach is a little bit less conventional because though it fulfills the needs of companies to have qualified workers, it negatively impacts unemployment rates, so many experts favor the people-centered approach over this one.
Important Cybersecurity Skills Needed
There are many traits that a qualified cybersecurity professional should have, but among the most important of these are (1) intrusion detection, (2) secure software development, and (3) attack mitigation. These are the three essential skills that will aid the cybersecurity industry in lessening the gap in qualified workers. “These skills were in greater demand than softer skills, such as the ability to collaborate, manage a team, or communicate effectively,” reports a researcher with the Center for Strategic and International Studies. While this may contradict what some people have previously thought, knowledge of these three main skills will ensure properly educated workers are placed in positions for which they are appropriately capable of fulfilling.
Because of its unpredictability, it is hard to say just exactly who will be right about the cybersecurity skills gap; however, peaking young people’s interest early and utilizing team work to bring together higher educators as well as industry giants might help for this gap to be lessened in the near future. If you are interested in a career in IT, visit us at https://axiomcyber.com/ to learn more about a small-business-centered cybersecurity career.
Hailey R. Carlson | Axiom Cyber Solutions | 9/23/2016