‘Tis the Season – The Season for Phishing
Christmas is coming early for phishing scam artists. The day after Halloween, my Inbox started filling up with alerts that I had won a $50 Amazon/Walmart/Costco Gift Card, packages I didn’t order began arriving from UPS/FedEx, LinkedIn change requests, and an assortment of other fanciful clickbait just begging to be clicked on.
Many of us are smart enough not to be fooled into clicking on phishing emails but a recent survey found that those of us who know the dangers of phishing still can’t properly identify 50% of phishing emails that are sent.
Even though surrounded by cyber-security day-in and day-out, one of our employees recently fell for a phishing scam for iTunes credentials. It wasn’t until their credentials failed to log them into the “iTunes” site and someone connected to their iCloud account that it dawned on them that they had been taken by a scam. Scammers are good and the reason why we continue to get emails from Nigerian princes and Nelson Mandela’s wife is that people still fall for the scams and cyber-criminals continue to make a profit.
Hackers are gaining easy access to money, user credentials, and healthcare data through a variety of different phishing scams. And they are sending out an estimated 8 million emails a week. The City of El Paso had $3.2 million diverted through a whaling scam that sent legitimate vendor funds to the incorrect accounts. Bayside Healthcare potentially revealed the health records of 13,000 patients by having one of its employees fall for a phishing scheme.
There is one simple step that everyone can take to defend themselves against phishing attempts: Hover over links in emails to see what site you are being directed to. Or even better yet, go directly to the vendor (Amazon, FedEx, banks, etc) to see if the offer or information is legit.
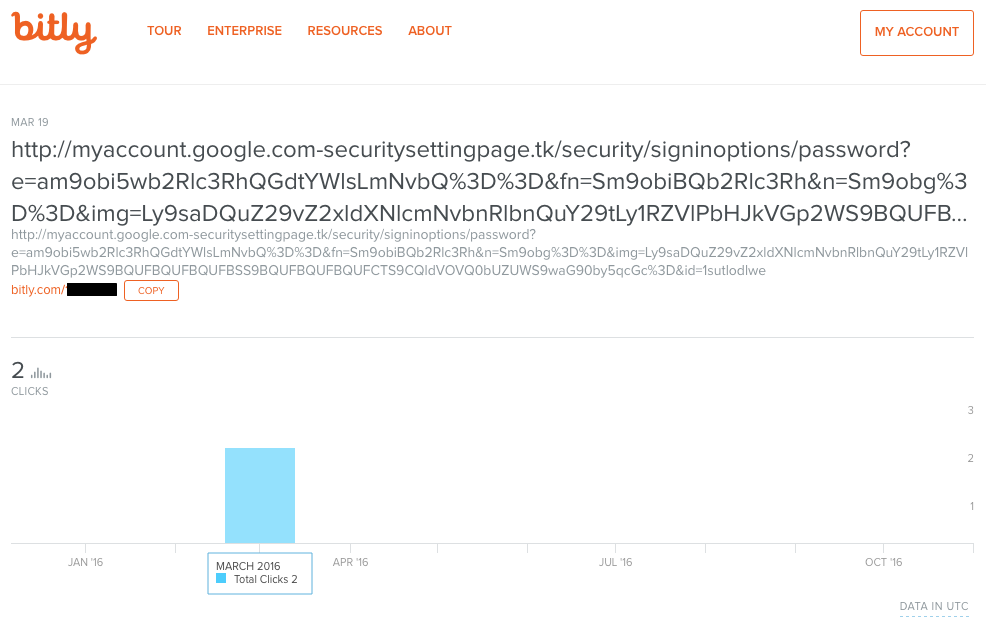
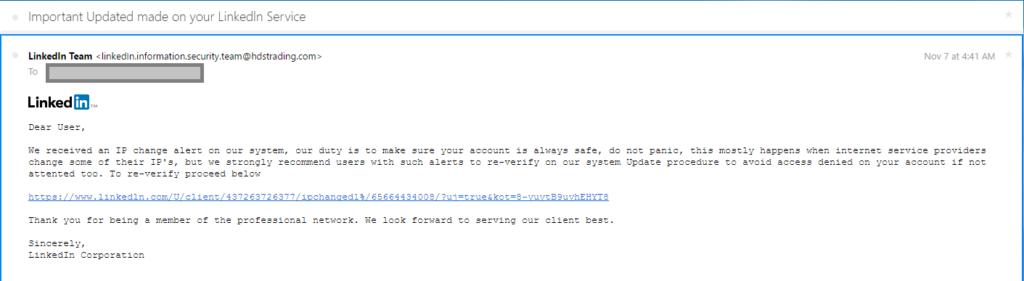
Clicking on links directly from emails, even if they appear to be legit, carries risk. The email that lead to the hack of John Podesta’s email came from a site that had an address that looked like it was part of the Google Domain but really was not.
Often I see emails that appear to be from banks with an odd misspelling (bankfoamerica.com or welllsfargo.com– Did you catch the problem?). Scammers have also been getting better at using proper English and grammar by hiring copywriters to make their emails more difficult to detect.
For business owners, implement a system of checks-and-balances for sending funds to vendors or distributing sensitive employee information. Encourage your employees to question unusual and urgent requests for wiring money, even it comes from the highest levels of the company because fraudsters are posing as the CEO, CFO, or HR Director to try to trick your employees.
Scammers take advantage of the whatever season it may be for soliciting for information. During tax season, they pretend to be the CEO or HR Director looking for employee W-2s. During the Christmas season, they send great sounding offers for gift cards and surprises from some of our favorite online stores to elicit information. So as the holiday shopping season is upon us, buyer beware… and buyer be wary. Scammers are out to get you and they are getting cleverer every day.




