Why Threat Intelligence is Not Always Intelligent
The primary purpose of threat intelligence is to help organizations understand what kind of threats they may face, zero-day attacks or exploits. The problem that exists for many organizations about threat intelligence is that there can be so much information coming at them, so much information to act upon, but no time or resources to shift through it, much less apply it to the company’s cybersecurity defense and/or strategy.
Threat intelligence that doesn’t do anything is not that intelligent.
Brent Watkins, FBI Special Agent (Retired), Axiom Cyber Solutions Head of Business Development
 There is a real issue with cybersecurity alert fatigue. It is such a problem that TechRepublic ran an article titled “Why notification overload is killing enterprise cybersecurity teams“. Cybersecurity fatigue affects 72% of organizations and part of the problem is the cybersecurity skills gap that only seems to be widening, rather than closing. Basically, the conclusion of a Bitdefender report called CISO’s Hardest Burden is that unless companies have enough personnel to deal with the incoming threat reports, they cannot improve their security.
There is a real issue with cybersecurity alert fatigue. It is such a problem that TechRepublic ran an article titled “Why notification overload is killing enterprise cybersecurity teams“. Cybersecurity fatigue affects 72% of organizations and part of the problem is the cybersecurity skills gap that only seems to be widening, rather than closing. Basically, the conclusion of a Bitdefender report called CISO’s Hardest Burden is that unless companies have enough personnel to deal with the incoming threat reports, they cannot improve their security.
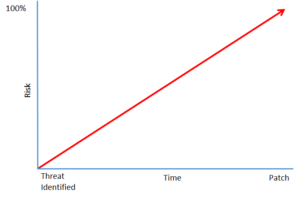 And if cybersecurity teams, or the lone IT professional tasked with anything & everything within the organization (including cybersecurity, which is not a hobby), are overwhelmed, what does that mean for the cybersecurity defense of the organisation? Troy Wilkinson, CEO of Axiom Cyber Solutions, has frequently discussed that a company’s risk factor exponentially increases from the time that a vulnerability is disclosed to the time that a patch is applied yet still so many organizations are struggling to stay on top of their cybersecurity defense.
And if cybersecurity teams, or the lone IT professional tasked with anything & everything within the organization (including cybersecurity, which is not a hobby), are overwhelmed, what does that mean for the cybersecurity defense of the organisation? Troy Wilkinson, CEO of Axiom Cyber Solutions, has frequently discussed that a company’s risk factor exponentially increases from the time that a vulnerability is disclosed to the time that a patch is applied yet still so many organizations are struggling to stay on top of their cybersecurity defense.
The result of the mismatch between the magnitude of threat data and the qualified resources needed to analyze and respond to new threats is increasingly costly and damaging data breaches across all industries from healthcare to financial services to retail and food service.
The problem with threat intelligence data is that it does require that someone in the organization to analyze and apply changes. Changes that may need to go through a strenuous and timely change management approval process which further slows down apply patches to maintain a secure cyber defense. And by the time that a change to the defense may be approved, there are thousands of other possible changes that have come through. So where does it end?
Axiom’s Polymorphic Threat Defense System
Recognizing the need to marry threat intelligence with action, Axiom Cyber Solutions developed its Polymorphic Threat Defense Systems used by both our Axiom SecureAmerica and Axiom Shield products. Axiom has curated over 100 open and closed sources of threat data to bring into our platform which allows us to currently push out over 350,000 threat data points a day to our clients. And to steal a line from “As Seen on TV”…but wait there’s more… one of the beautiful things about connecting with Axiom’s platform is that it requires no action on the part of the customer. All updates from our platform are fully automated and applied without intervention.
Threat actors are constantly evolving their tactics, methods, and connection points. It is important that we also evolve our defenses just as fast, if not faster, to ensure that we are doing our best to protect our businesses.
If you are interested in more information about Axiom’s Polymorphic Threat Defense System, please contact us or call 800-519-5070.

